U.S. Air Force and University Scientists Share Their Vision for Unconventional Computing
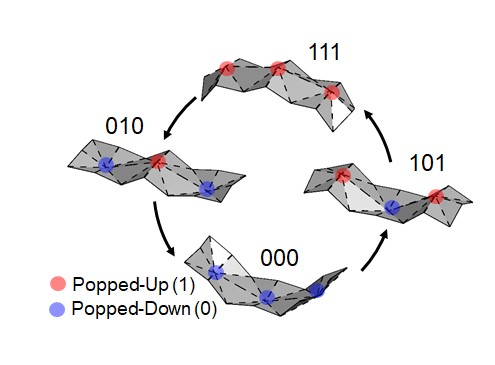
Conventional computing hardware represents information as ones and zeros, depending on the state of electronic transistors. This creates artificial bottlenecks in the flow of information processing by first requiring that environmental loads be converted into an electronic state and second by routing the information to centralized computers for processing. Researchers from Wright-Patterson’s Air Force Research…