Introduction
April 2007 marks the month when the internet became weaponized [1]. In Estonia’s capital city of Tallinn, the government decided to move a bronze statue of a Russian soldier from the city center to a war memorial cemetery on the outskirts of town (Figure 1). They wanted to move the statue during the 60th anniversary of its erection in 1947, which memorialized the sacrifices of Russian soldiers liberating eastern Europe from the Nazis.

Figure 1. Russian Soldier Statue (Source: Postimees/Scanpix).
Amidst protests, a targeted distributed denial of services (DDoS) attack struck banking, government websites, and small businesses, taking these government and commercial services offline for several weeks. The Estonian government brought services back online, but this event marked the first time the world had seen a “cyberattack.” Leading experts attributed this DDoS attack to Russian organizations. Fourteen years earlier, another momentous cyber event took place but was not limited to just Estonian citizens—this event changed the world forever.
The World Wide Web (WWW) became first available for public use and consumption in April 1993 [2]. It was the brainchild of researcher Tim Berners-Lee while working at CERN, a Swiss physics lab. But the original internet, predating the WWW by 24 years, was a military invention called the ARPANET [3]. Built in 1969, the ARPANET demonstrated data being transferred via computers outside a local network for the first time. Its name came from an agency called ARPA, predecessor of the Defense Advanced Research Projects Agency (DARPA). Even though the United States has had an internet since 1969, when the WWW opened its aperture to the world, the public and private sectors became so interconnected that it is now considered by some countries as a human right.
From its earliest days, organizations utilizing the ARPANET’s data transfer capability knew each other when they communicated on the network, and trust was implied. But since the opening of the WWW, there has been more ambiguity to who or what is on the other side as well as their desire for others’ devices. Hacking from lone wolves to nations’ states is now prevalent across this new domain, and for the last 15 years, countries have used it as a statecraft for espionage and warfare.
Estonia marked the beginning of weaponizing cyberspace, but no permanent damage has been associated with this disruption. In 2010, we saw physical destruction of machines. A joint American/Israeli operation called Olympic Games used a cyber tool called Stuxnet to destroy Iranian nuclear centrifuges. In this operation, we saw damage in the physical world from the virtual environment [4].
In this new world order, modern militaries are seeing their networks, weapons systems, and infrastructures become vulnerable to these types of cyberattacks. Defined by the National Institute of Standards and Technology, a cyberattack is “an attack, via cyberspace, targeting an enterprise’s use of cyberspace for the purpose of disrupting, disabling, destroying, or maliciously controlling a computing environment/infrastructure; or destroying the integrity of the data or stealing controlled information” [5].
U.S. Air Force (USAF) Integrated Cyber Defense Strategy
Just like the rest of the world, the USAF learned that the cyberspace network is the backbone infrastructure for other organizations to use in creating weaponized cyberspace effects. In 2016, they started transforming their legacy communications squadrons to cyberspace operations squadrons. They called this transformation the Cyber Squadron Initiative (CSI) [6]. For example, a USAF pilot operates the aircraft but does not fix it; an aircrew member is the operator of the weapons system, not the maintainer. In the same vein, the communications squadrons are the maintainers of the network. These new cyberspace operations squadrons would become the “pilots,” or operators, in this new domain. They would have to gain new trade skills and experiences, utilizing their computers as weapons inside the network. The Cyber Squadron Enabling Concept, signed in 2018, and the Program Action Directive for CSI, signed in 2020, finalized the creation of these teams and processes. The USAF created operational units called Mission Defense Teams (MDTs) to defend their interconnected assets in cyberspace. This concept was built on integrated cyber defense [7].
Integrated cyber defense is a layered model that provides three key components: proactive defense, resiliency, and defense in depth (Figure 2). Proactive defense is human cyber defenders seeing potential cyber adversaries in their communications and weapons system networks. These defenders can prevent and fight off cyber intrusions. Resiliency is the idea of building or improving these systems, or processes, during a conflict. And defense is the layered, automated, or semiautomated tools to initially block intrusions.
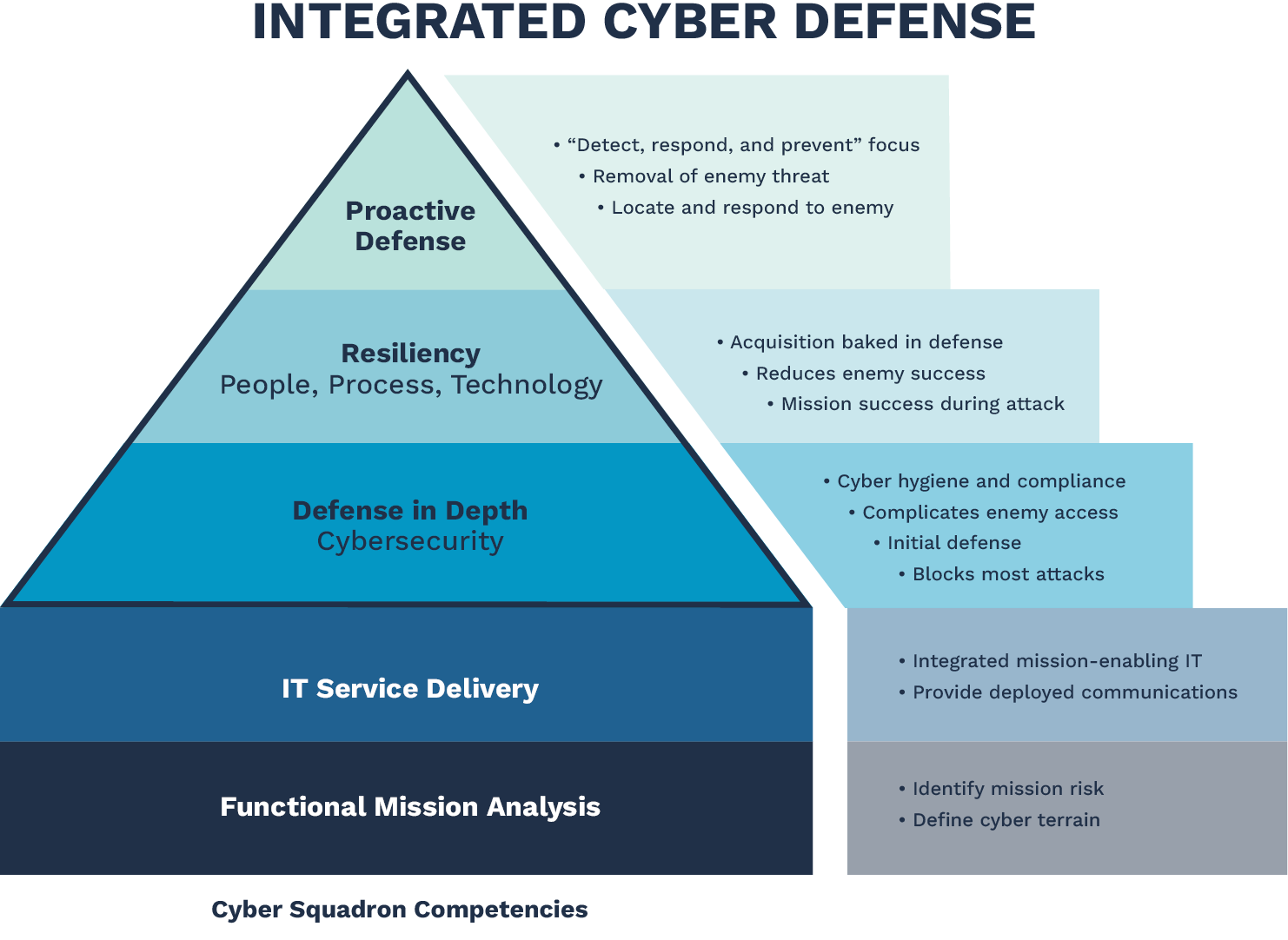
Figure 2. Cyber Defense Layered Model (Source: U.S. Air Force).
The foundation of this defense is placed upon the network infrastructure, called information technology (IT). Functional mission analysis cyber is a sublayer to this foundation that identifies risks and where that risk (cyber terrain) goes in the mission.
The concept and model of integrated cyber defense is solid. Combining humans and machines to defend cyberspace makes total sense when facing today’s cyber challenges.
Challenges and Opportunities
The USAF’s first challenge in its cyber defense strategy was to move the military members from communications to cyber operations. They created the MDTs to host the new cyber operations squadrons. However, people still needed to take care of the network, so they invested into Enterprise IT as a Service (EITaaS) in 2018 [8]. EITaaS is the process of contracting network maintenance out to companies, but it comes with a $6B bill.
That same year, the USAF consolidated all cyber equities to the Air Combat Command and created a three-star numbered air force called 16 Air Force (AF) a year later. The 16 AF combined intelligence and cyberspace into one area. By 2022, there were 84 MDTs across the AF bases, or wings. The USAF is the only service invested in this type of cyber defense at the base level and controlled by the base commander for their wing priorities. This year, they divested most of the teams and only funded 19 of them. What happened? We will explore factors that possibly contributed to this in the following sections.
Integrated Defense Model
We will discuss each area of the integrated defense model and what improvements can be made to salvage it and make it a combat-effective capability for the USAF.
Proactive Defense
Proactive defense is given to the base or wing commander, a colonel most likely, who has no formal education in cyberspace and is usually a legacy operator of an aircraft or missile system. Many of these commanders do not even know they have MDTs on their bases, nor do they know how to utilize them. As a result, MDTs are not executing mission-relevant operations and are still inside their communications squadrons, residing at the mission support groups and away from the operations groups. Since support groups are there to support wing functions like computer repair or network outages, many MDT members are still doing legacy support, even with EITaaS at their bases.
MDTs are not sent to a formal training school like aircrews. When attending formal training schools, aircrews not only learn about their aircraft but how to employ that weapons system in a combat environment where multiple effects are taking place. They know where their combat capabilities fit into the larger war effort. Flying is the easy part; combat employment, in context of a highly contested environment, is the tougher skill to learn. In contrast, MDTs are getting computer-based training, which involves a few weeks of understanding cyber tools to utilize in defense and learning how to assess risk in their networks, including weapons systems and base infrastructure.
The higher command has never issued a timeline to complete training or execute first missions. Some teams have stayed in the training pipeline for years, never converting to being fully mission qualified. The return on investment of these teams to show mission effectiveness in cyber defense of a base was very low. Of the teams that showed effectiveness, the secret sauce was two-fold—wing leadership buy-in and understanding the importance of cyber defense as well as integrating these MDTs into all aspects of their base mission, including operations, maintenance, support, and intelligence. The teams met regularly with their counterparts and debriefed wing leadership on their mission status and the priorities their wing commanders gave them.
To improve their effectiveness, the MDTs must be held accountable to a timeline for mission qualification, which is the responsibility of the Air Combat Command. In addition, the Air Education and Training Command, particularly Air University, needs to offer cyber education to new wing and group commanders when all new commanders go to Maxwell Air Force Base in Montgomery, AL, for their required courses. MDTs need their own formal training unit, and when arriving at their base, they need mission qualification training for their base mission (fighter, bomber, missile systems, etc.). Integration at the wing level and into all exercises and training opportunities is necessary since all other wing units do this.
Resiliency
Resiliency is not addressed in the integrated cyber defense model. There is a complete misunderstanding of mission risk, which is defined in simple terms as a threat acting upon a vulnerability [9]. To quantify risk, there is the evaluation of consequence and the likelihood a negative event would take place. Risk assessments usually only incorporate one system or domain. However, when using system theory, mission risk pertains to a system of systems needed to operate in any complex environment, including combat. Most cyber risk assessments would showcase one area—outdated servers or unpatched computers. All servers need electricity, air conditioning, physical security, and connectivity to the computers they are interconnected with. Servers operate in a system of systems. For example, if an air conditioning unit was 20 years old, instead of updating a 3-year-old server, the air conditioner should be fixed first before the servers overheat when the unit breaks down.
Also, integrating and including the intelligence community into these risk assessments is necessary because not all vulnerabilities are acted upon. Intelligence, just like battlefield assessments of enemy missile and aircraft systems, uses this to understand weaknesses and prioritize courses of action for decision-making. Cyber defense is no different.
A better way to view cyber risk assessments is understanding the mission first and what pathways the systems utilize to execute that mission. Fusing the MDT with operations, maintenance, and intelligence when those risk assessments are being made allows risk to become mission risk; risk is now in context. Two other important risk areas involve the enemy and one’s own system. For example, in cyber defense, we have learned over the years that China steals intellectual property vice Russia that disrupts allies’ systems. Those are two completely different focus areas—the cyber defense teams and the tools needed to defend those networks. Knowing one’s systems and which has the most vulnerabilities are key factors when performing these assessments. Cyber teams and IT professionals do not own risk. They advise on risk. Leaders and commanders own the risk. Cyber teams are there to inform and help leaders prioritize risk so the entire base can execute the missions.
Defense in Depth
Defense in depth is not being optimized. The USAF is the one service that loves its technology more than its sister services. But even beyond the military, in the cyberspace domain, technology is king. Terms like artificial intelligence, quantum computing, and machine learning have taken over from yesterday’s outdated lingo like zero trust and blockchain. The military uses technology to fill in its capability gaps. They should be asking, “What is the mission, what are the capabilities we need to execute that mission, and can technology answer these gaps in mission execution?” This is the starting point when finding technology that works for mission relevancy.
Retired AF Colonel Tony Franks once heard an AF general say to blockchain the entire Air Force [10]. This is probably not feasible because blockchain is a distributed database utilizing ledgers and timing, so one cannot easily manipulate a tasking [11]. However, when time is of the essence, like that involving nuclear weapons or combat search and rescue of a downed aircrew member, there should not be a delay in executing these missions for national security. On the other hand, acquisitions, lifecycle management of systems, and contracting can be blockchained. We should use the right tool for the job—the right technology for the mission requirements.
Beyond technology are people. Knowing the enemy is critical, but knowing the people is more important. Cybersecurity is vital to our missions in the military, and industry has handled it through automated and semi-automated defenses and tools. There have been more cybersecurity violations from negligent users than any enemy lurking in the cyber shadows. We need to increase, improve, and update our cybersecurity training in the services. Education is the cheapest way to defend ourselves in this domain. Because leaders have different training and education needs than their subordinates, airmen should have multiple training venues that take them on a cybersecurity journey through their entire career, from basic cyber hygiene to advanced awareness and tactics. In addition, members of a wing should get classified briefings on enemy cyber capabilities and their own weapons system vulnerabilities.
Conclusions
The USAF should be the most lethal airpower component in the world. This world is completely interconnected in cyberspace, and cyber defense is an incredible challenge. The old world saw that a good defense could always outlast an invading army. In this new world order, cyber offense just needs a single avenue to get through a layered cyber defense. There will never be a perfect cyber defense, but we should not make it easy for the enemy. The goal of the AF Integrated Cyber Defense Strategy should be to make adversarial cyber intrusions so difficult and expensive to conduct that the adversary does not want to attack due to the combat cost. Addressing these challenges, we can implement that strategy effectively for our nation.
Note
This article is the opinion of the author and does not represent the views of the U.S. government, USAF, or Air University.
References
- Ottis, R. “Analysis of the 2007 Cyber Attacks Against Estonia From the Information Warfare Perspective.” Proceedings of the 7th European Conference on Information Warfare and Security, Plymouth, pp. 163–168, 2008.
- NPR. “30 Years Ago, One Decision Altered the Course of our Connected World.” https://www.npr.org/2023/04/30/1172276538/world-wide-web-internet-anniversary, accessed 17 July 2023.
- DARPA. “ARPANET.” https://www.darpa.mil/about-us/timeline/arpanet, accessed on 17 July 2023.
- CSO. “Stuxnet Explained: The First Known Cyberweapon.” https://www.csoonline.com/article/3218104/stuxnet-explained-the-first-known-cyberweapon.html, accessed on 17 July 2023.
- NIST. “Cyberattack.” https://csrc.nist.gov/glossary/term/Cyber_Attack#term-def-text-1, accessed on 17 July 2023.
- USAF. “Cyber Squadron Initiative: Arming Airmen for 21st Century Battle.” https://www.af.mil/News/Article-Display/Article/1174583/cyber-squadron-initiative-arming-airmen-for-21st-century-battle/, accessed on 17 July 2023.
- USAF Headquarters. “Cyber Squadron Initiative.” https://www.dafitc.com/wp-content/uploads/Cyber-Squadron-Initiative.pdf, August 2018.
- USAF Materiel Command. “ETIaaS Wave 1 Services Awarded in $5.7B Agreement.” https://www.afmc.af.mil/News/Article-Display/Article/3377827/eitaas-wave-1-services-awarded-in-57b-agreement/, accessed on 17 July 2023.
- Washington University St. Louis. “Vulnerabilities, Threats, and Risks Explained.” https://informationsecurity.wustl.edu/vulnerabilities-threats-and-risks-explained/, accessed on 17 July 2023.
- Franks, T. Personal communication. AF Center for Strategy and Technology, 31 August 2023.
- Investopedia. “Blockchain Facts: What Is It, How It Works, and How It Can Be Used.” https://www.investopedia.com/terms/b/blockchain.asp, accessed on 17 July 2023.
Biography
Anthony Franks is an Air University professor who teaches at the Chief of Staff of the AF’s academic fellowship, Blue Horizons, where he educates battle-ready entrepreneurs capable of leading positive, disruptive change by creating and testing prototypes for combat viability. His focus areas are military cyber operations, special operations in grey zone warfare, and joint military warfare. He served 24 years in the USAF as a pilot and cyberspace operations officer and taught cyber operations education for five years at the USAF Cyber College. Col. Franks holds a B.S. in business management, an M.A. in military strategy, and an M.S. in theology.


