The concept of “Key Cyber Terrain” has gained popularity within the Cyberspace Operations community. The term is used as an analogy to the more traditionally familiar concept of “Key Terrain” that is utilized by commander’s to identify physical terrain features (hills, mountains, choke points, etc.) that can provide military advantage.
While conceptually simple to understand, applying this concept to cyberspace has proven to be challenging. This is because cyberspace has properties that do not translate well to the physical world. These differences manifest themselves in multiple, sometimes subtle, ways that quickly break the analogy and hamper our ability to define what truly constitutes “Key Terrain” within this domain, and how to best identify it. This does not mean we have to completely abandon the concept. We do, however, need to be aware of the analogy’s limitations, and reach a consensus as to what is truly meant by the term “Key Cyber Terrain”. More importantly, we need to understand the benefits that can realistically be gained from its identification during planning and mission execution at various operational levels.
Introduction
“Key Terrain” is defined as “Any locality, or area, the seizure or retention of which affords a marked advantage to either combatant. (JP 2-01.3)” [1]. The value of terrain in support of defensive and offensive military operations has been known for millennia1. In a defensive context, for example, narrow ingress passageways can be used to mitigate a force with superior numbers. From an offensive perspective, avoiding terrain that hampers movement and using land features to protect your flank can significantly improve mission success [2]. The ability to identify such terrain features within the operational environment allows commanders to more effectively plan and tailor their efforts. To simplify some of the complexities of cyberspace, we attempt to make analogies to the physical world that allow us to apply familiar doctrinal processes. The concept of “Key Terrain” is one such construct that has manifested throughout the community as “Key Cyber Terrain” or “Key Terrain within cyberspace” [3] [4].
To simplify some of the complexities of cyberspace, we attempt to make analogies to the physical world that allow us to apply familiar doctrinal processes. The concept of “Key Terrain” is one such construct that has manifested throughout the community as “Key Cyber Terrain” or “Key Terrain within cyberspace” [3] [4].
A common theme that seems to be shared amongst all practitioners, is that “Key Terrain” should be directly linked to mission objectives. This is relatively intuitive given that terrain that is advantageous to one side for some operational scenario is obviously a disadvantage to the other. Another agreed upon attribute is that its value is temporal; coupled with the duration of a mission. For instance, fighting from an elevated position (high ground) is beneficial for a number of reasons. Holding higher ground provides an elevated vantage point with a wider field of view. Soldiers fighting uphill will move more slowly and tire more quickly, and so forth. However, depending on the timeframe, seizing the high ground is not always advantageous. If an opposing force has the time and capacity, they can surround a well-entrenched adversary, cutting off resupply and essentially just “wait them out”2.
Applying both of these requirements to “terrain” within cyberspace seems straightforward. When executing a certain military operation, only portions of this virtual domain will be important or advantageous; changing over time based on mission timespan or as the mission evolves. But, what within cyberspace equates to “terrain”? How do we identify what aspects are advantageous in support of a specific mission? Even more troubling, how do we even scope a “mission”? Defining a mission too broadly, (e.g. maneuver to, seize, and secure objective TANGO), quickly renders the problem of identifying all essential cyberspace resources intractable [5]. Conversely, define a mission too granularly (e.g. fuel my vehicle now) makes it easy to bound, but causes excessive vacillations on what is important as we switch across a large set of tiny concatenated tasks.
These open questions are further complicated by the fact that warfare within the Cyberspace Domain has undeniable dissimilarities from the more traditional physical domains of land, maritime, air and space [6] [7]. These differences have proven to be of sufficient complexity to keep “Cyber Key Terrain” an elusive concept that is yet to be consistently defined or fully understood.
Analogy Breakdown
This article presents multiple aspects of cyberspace, and associated challenges, that are hampering our ability to apply the concept of “Key Terrain” within the domain. These include: differences in what constitutes terrain and associated fundamental properties, inconsistences in definitions, challenges pertaining to the visualization and understanding of cyberspace, incongruence in the identification of mission critical systems vs. overall security risks, difficulties in bounding the problem when applying the concept to a complex system, and nonequivalence when attempting to utilize the concept to prioritize resources.
What is “terrain” in cyberspace
Before we can begin any discussion on the identification of “Key Cyber Terrain” we must first answer the more fundamental question of what is “terrain” within this virtual man-made environment. Surprisingly, not much has been written on this topic. Most existing literature seems to operate on the assumption that cyberspace terrain is simply the systems, devices, software and interconnections that constitute cyberspace itself. Raymond et all [4] are among the few that attempt to provide a formal definition:
“The systems, devices, protocols, data, software, processes, cyber personas, and other networked entities that comprise, supervise, and control cyberspace”
This characterization seems to follow the philosophy that terrain within cyberspace is basically anything and everything that makes up, or is a part of, the domain.
Comparing to the physical world, terrain is defined as:
“A stretch of land, especially with regard to physical features3”.
While military doctrine does not formally expand on this definition, in practice “Key Terrain” is understood to include both natural land features as well as man-made objects, such as bridges, buildings, or more strategic elements such as ports and cities, which can also provide military advantage.
Comparing these two definitions, one can already see some significant differences. Within the physical world, terrain is a finite subset of the domain. For instance, there is a clear differentiation between what is a terrain feature vs. what is a military asset (i.e. a valley or a bridge vs. a tank or a plane). Within cyberspace, this distinction no longer exists. The ability to easily differentiate between terrain features vs. assets is lost. The provided definition even includes cyber personas, in essence encapsulating virtual individuals as part of the terrain landscape. This fundamental expansion of what constitutes “terrain” within cyberspace, results in numerous ambiguities and interdependencies, which make identification of “Key Terrain” within it very challenging.
Inconsistences in defininng “Key Cyber Terrain”
No official doctrinal definition of “Key Cyber Terrain” exits. To bypass this discrepancy, the term “Key Terrain within cyberspace” is gaining popularity. In this context, the well understood definition for “Key Terrain” is directly applied to cyberspace equivalent to the other domains. While this approach appears reasonable, as previously discussed, it fails to acknowledge that “terrain” in cyberspace is much broader in context.
Regardless of semantics, the concept of “Key Cyber Terrain” is most often used to signify the physical and logical elements within cyberspace that are critical enablers for the successful execution of a mission4[8]. Within this context, some have postulated that “Key Cyber Terrain” is simply a subset of the broad categories of hardware and software components that are essential for the execution of a particular mission. These can include such things as physical and transport layer infrastructure (e.g. undersea cables, service providers), computing and data centers, or key services (e.g. Domain Name Service), to name a few [3] [4]. Others have equated “Key Cyber Terrain” to critical capabilities or assets that support a specific type of military operation (e.g. Fires => AFATDS5 or Missile Defense => BMDS6) [9] [5]. Both approaches are limited in their usefulness [7]. In the first case, “Key Cyber Terrain” becomes too abstract or diffuse of a concept, quickly extending beyond the area of operations for all but the most strategic of commands. In the latter, “Key Cyber Terrain” is oversimplified to mean a specific mission enabling application or system. This view of terrain does not have the same context as its physical counterpart, and is in essence equivalent to claiming a tank or a ship (regardless how important it is to the mission) is “Key Terrain”. Physical terrain does not in itself provide a capability. It provides military advantage, enhancing the effectiveness of capabilities you already possess, or tactics you employ. If the physical components of systems such as AFATDS or BMDS are not “Key Terrain” in the land domain, then why should their logical representations within cyberspace be?
Differences in the fundamental properties of “terrain”
Terrain features in the physical world have intrinsic properties that are well defined and understood. Mountains and swamps are hard to cross, dense vegetation provides obscurance, and hilltops provide a better field of view. Each of these properties is immutable. Their value to a military operation is only dependent on their geographical position relative to the intent and duration of a particular mission.
It can be argued that certain devices or services within cyberspace provide functions that imbues them with some fundamental characteristics that are comparable to the examples provided above. For instance, a router by design has access to a large amount of network traffic. The more principal the router (core backbone, country gateway, etc.) the more traffic it can “see”. So are routers in cyberspace then analogous to high ground, providing varying levels of increased visibility?
The analogy does seem to be intuitively sound, but there are still some fundamental differences. Though a router does provide the ability to observe more network traffic, this does not really translate to the same type of visual awareness that a hill can provide. This is because network traffic flows are comparatively much more complex. For instance, their point of origin and destination are at times obfuscated, and can extend well outside a commander’s area of interest without any simple mechanisms for determining which are of relevance (especially at lower echelons).
More importantly, current operational policies and rules of engagement limit how such cyberspace terrain can be leveraged. A tactical commander does not have the authority to commandeer a network router7 as they do a hilltop within their Area of Operation. This is a core fundamental difference in the analogy that is often overlooked. As discussed in [4], “Key Terrain” in kinetic warfare spans tactical, operational, and strategic levels, but it is most commonly applied at the tactical edge. At these lower echelons, a commander can readily take advantage of terrain features within their purview to the benefit of the mission. Within cyberspace, this model is reversed. The steep Intel requirements necessary to understand cyberspace, coupled with its geographical ambiguities and legal restrictions, make the concept hard to apply at the tactical level without significant higher echelon, or even strategic level support.
Challanges with visualizing and understanding cyberspace
When identifying “Key Terrain”, a tactical commander can look at a map and readily recognize land features that can provide advantage or disadvantage for a particular maneuver operation. These structures can be within friendly, neutral or adversary space. They may be currently uncontested, or under direct enemy control. While cyberspace has many of these same properties, they are much harder to understand and visualize. For instance, determining if an adversary controls some device or service within cyberspace can be difficult to ascertain as it does not necessitate the physical occupation of some geographical region [4].
In some respect, the concept of “Key Cyber Terrain” highlights some of our current capability gaps with the domain. For example, logically mapping all of cyberspace within an area of interest is highly challenging from a purely technical perspective8. In addition, features within cyberspace that may be potentially relevant to a military operation cannot be easily mapped or confined a tight geographic boundary. Such limitations significantly hamper a commander’s ability to identify what portions of cyberspace, within their purview, are important to their mission.
Because of these barriers, we often artificially limit the scope of “Key Cyber Terrain” by primarily looking inward, to military systems and networks (“Blue” space) that are under a commander’s direct control. Even this, however, has proven hard to do9, and thus, often deteriorates even further to the identification of mission critical assets. Applegate et al. [7] states the following on the matter:
“…defining and protecting critical assets should not be confused with identifying “Key Terrain”. Understanding how the identification of critical assets shapes the identification of key terrain during a mission is important to the success of our cyberspace planners. This process allows planners to prioritize critical assets, create a Critical Asset List, determine which assets should be defended, develop a Defended Asset List, and then identify key terrain in relation to these assets and mission objectives.”
While this statement takes a strong position on how the identification of critical assets is not equivalent to “Key Terrain”, it does little to explain what “Key Cyber Terrain” is. One can even argue that this assertion makes it hard to see what additional value the concept provides beyond everything that was previously listed.
Incongruities between the criticality of a system vs. overall risk
From a Defensive Cyberspace Operations (DCO) perspective, limiting the concept of “Key Cyber Terrain” to mean just critical, or high value, systems and service (as proposed in [5] [9]), can actually provide a false sense of security. The criticality of a system to a specific mission does not necessarily equate to what constitutes its highest security risk [10]. This is especially true when dealing with a complex system with intricate interdependencies.
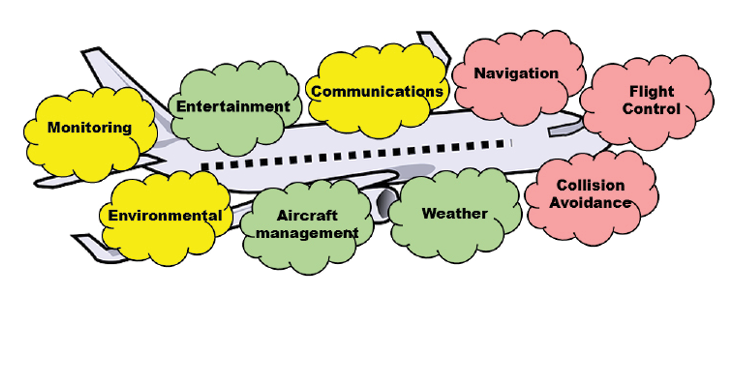
Figure 1. Example aircraft control systems, color coded by importance during flight (red = high, yellow = moderate, Green = low) – Source: Author
For example, consider a modern commercial aircraft as depicted in figure 1. This airplane contains multiple control systems. Clearly, some are more important than others during flight. These subsystems, however, are not fully independent. For instance, collision avoidance must be able to communicate with flight control to redirect the aircraft in an emergency. Flight control must be able to communicate with navigation to maintain heading, and so on. These interdependencies are so pervasive, that most aircraft are equipped with a variety of common communication buses and protocols10 that interlink almost all such subsystems in a standardized manner. From a computer security perspective, this renders their relative functional importance potentially irrelevant. In May of 2015, cybersecurity consultant Chris Roberts claimed to have been able to take control of an aircraft’s engines via the onboard entertainment system and cause the plane to climb during flight [11]. This was later debunked, as the entertainment system within the aircraft fortunately did not have any connectivity to flight control systems [12]. But, had there been11, would anyone have had reason to consider the entertainment system as critical to flight? In the now infamous Target Corporation Point-of-Sales compromise that resulted in 10’s of thousands of stolen credit cards12, can anyone within Target’s senior management truly be blamed for not having considered connectivity to a low priority, 3rd party, refrigeration contractor as “Key Terrain” within their enterprise network13?
Difficulties in bounding the problem within a complex system
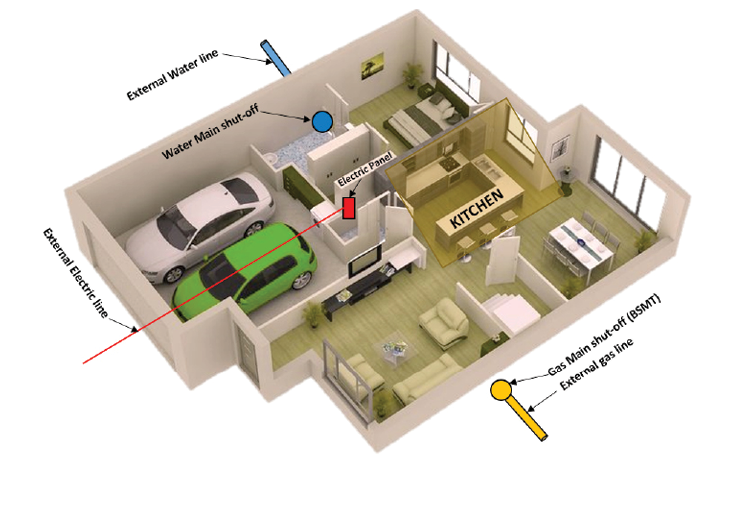
Figure 2. Model of a typical home – Source: Author
Another fundamental property of physical terrain is that they are “simple” closed systems bound in three dimensional space. A hill, after all, is just a hill, and as such, possesses certain “hilliness” attributes that can be beneficial or detrimental depending on the use case. It is, in large part, this simplicity that allows a tactical commander to readily identify “Key Terrain” within a traditional military context. However, when the concept is applied to a complex system, the problem can rapidly become intractable. To better illustrate this, consider the following scenario:
Your mission is to cook dinner tonight in the home depicted in figure 2. You have all the ingredients you need within the kitchen, and you identify the stove and the oven as critical systems you must maintain control of and keep functioning.
Given this relatively simple situation, what is the “Key Terrain”? Clearly the kitchen itself is of critical mission importance. We can ensure we block off and guard all physical avenues of approach to this space relatively easily, but is that sufficient? As it turns out, the stove runs on natural gas, the oven on electricity, and we also need water (a critical ingredient for the planned meal). Gas and water shut-off valves, and the electrical panel, are in different rooms within the house, so we need to protect them as well. What about the gas, power and water lines that run external to the home? What about the power distribution center that serves the neighborhood? Do I need to protect that as well? What about the water reservoir that serves the town14?
When applied to a complex system, what comprises a critical resource is hard to bound; continuing to expand further and further away from what is in our direct control as dependencies branch outwards15. The situation can be made even more complicated by simply increasing the mission’s execution time. For instance, what if the mission was to cook dinner every night for a month? Now we would also need to worry about obtaining resupplies, and ensure all the things that enable us to procure and transport them also remain available to us.
Unfortunately, most elements within cyberspace are, or are part of, a complex system that is not encapsulated within three dimensions, but rather some potentially uncountable number. This complexity, as illustrated by this simple example, manifests as a number of interdependencies that hamper our ability to bound the critical resources essential for mission success, or to identify aspect of the environment that may offer some advantage.
Nonequivalence in the ability to prioritize resources
One of the desired benefits obtained from the identification of “Key Cyber Terrain” is an ability to focus available resources on what is most important or advantageous for a mission’s success. Within the more traditional physical domains, this trade-off analysis occurs almost naturally. When a commander identifies “Key Terrain” features they want to either defend or obtain control of, anything that remains are by default portions of the operational environment that, if necessary, they would be willing to cede to the adversary. This same tradeoff is not as clear when working with complex systems, as is the case for practically all cyberspace operations.
For example, let us revisit the scenario presented in section II.F. To truly guarantee mission success, we need a way of encapsulating everything we require to accomplish the mission into a closed self-contained system. But, even if we devise some means where we can cook dinner in the kitchen completely segregated from any external need (I have an electric generator for the oven, I stored enough water for my needs, I have a portable gas canister for my stove), does this mean we are willing to ignore all other things that are not currently essential? For instance, are we willing to let an adversary steal the cars from the garage because we do not need them at this time? Likewise, does identification of “Key Terrain within cyberspace” imply that we are willing to deviate network security focus and/or resources in a manner that can potentially allow an adversary to compromise other network systems that are not directly supporting the current mission16?
Re-Interpretation of the Concept
The previous section has identified several challenges associated with trying to directly apply the concept of “Key Terrain” to cyberspace. In summary, as currently defined, terrain within cyberspace encompasses all things that constitute the domain. As a result, it is difficult to differentiate between “terrain” elements that provide advantage and individual assets or capabilities that are important for the execution of a specific mission. Practically all systems within cyberspace are complex in their function and often possess multiple external dependencies. As such, it is not enough to protect what we identify to be mission critical systems. We also need to consider all the data sources and communication links such capabilities rely on to function, and ensure those too maintain availability and data integrity. Even more problematic, any existing communication or access path to a system can serve as an attack vector with potentially greater security risk. If the mission is a prolonged campaign, then we would also need to protect all the logistics systems necessary for sustainment and resupply. And, even if we could do all these things, this does not imply that we can deviate resources away from other systems in a manner that may make them more susceptible to (or us less aware of) their potential compromise. Expanding to more offensive operations, which have to consider both civilian and adversary cyberspace networks and capabilities that are outside our direct control, makes these challenges even more pronounced.
This all leads to the inescapable conclusion that the concept of “Key Cyber Terrain” needs to be re-interpreted to deal with the complexities of the domain. A simplistic, but clearly sub-optimal, approach could just entail a re-definition of the term. For instance, if we indeed wish to equate “Key Cyber Terrain” to mean “Mission Critical Cyber Assets” (across blue, gray and red cyberspace), then we should clearly state this in doctrine, and then ensure we understand and agree on its use cases, benefits, and limitations.
A more interesting approach, is in the realization that “Key Cyber Terrain” may not necessarily be something within cyberspace that you identify, but rather something that must be created. Cyberspace is, after all, a virtual man-made domain. It is therefore reasonable to assume that “Key Terrain” within it may not naturally emerge, but must instead be explicitly architected within it17. In our previous aircraft example, having the ability to decouple individual subsystems from each other did allow for the identification of more important functions during flight. Even in our “cooking” example, we were able to devise a means to negate the need for certain critical mission resources that were outside our direct control. Achieving this, however, is not a trivial matter. Such segregation of functionality has to be explicitly designed within a system’s architecture, through well-defined boundaries and interfaces that guarantee certain behavioral properties and protections, which are then enforced in implementation. As an example, [5] describes the challenges associated with mapping a mission to its required network resources. They even postulate that it may be impossible to do so with high fidelity within existing networks. However, they do hypothesize that establishment of a “Mission Aware Network Architecture” would allow for the automated tracking of data flows and system interdependencies to facilitate this mapping process. Given we cannot start from scratch and completely redesign all Army networks, we can begin by investing resources to obtain a much more detailed understanding of our networks as they exist today. If we can fully enumerate all interdependencies between systems and mission sets, we can then attempt to define and enforce strict boundary controls between core components, potentially creating “Key Cyber Terrain” in the process.
A last point for consideration is that perhaps, as the proverb says, the journey is more important than the destination. Application of the OCOKA18 process to cyberspace as explained in [4] [14], appears in itself to be highly beneficial. By following this process in a methodical manner, the end state is that we have conducted a fairly detailed mission capability, threat, and risk assessment. Subsequent studies of the previously discussed Target attack have revealed many ways the company could have prevented the compromise from happening [13] [10]. None, however, relied directly on the concept of identifying “Key Terrain within cyberspace”. Instead, they champion the institution and application of a comprehensive risk management process that, much like the OCOKA model, allows security experts and managers to systematically analyze their entire enterprise network and identify all potential security risks and weaknesses. Somewhere during the execution, or at the conclusion of such an analysis, we may be able to point to certain aspects of the network which we deem to be “Key Cyber Terrain”, but in reality, it was the application of the process that provided most of the benefit.
Further Research
We acknowledge that this article does not provide definitive answers to the fundamental question of what is “Key Cyber Terrain”, or how to identify it. While we have made a few key observations and recommendations, we do agree that much more remains to be done. The intent of this article was to clearly articulate the fundamental properties of cyberspace that are preventing us from being able to readily apply the analogy. It is hoped that this will enlighten, and inspire continued conversation and research on the topic.
In the process of writing this article, what became increasingly clear is that we lack concrete use cases. Creating a set of detailed scenarios from which we can then attempt to identify “Key Cyber Terrain” as part of a well-defined process will be highly beneficial. Scenarios should be varied to include direct support to a tactical maneuver or engagement, as well as more strategic pre-phase three operations19. Scenarios should also include both defensive and offensive components. A final interesting observation, is that we have a propensity for applying the concept of “Key Cyber Terrain” across operational domain boundaries. In other words, we most often want to know how cyberspace operations can support traditional physical mission sets. It would be interesting to see if any of the challenges that have been presented in this document are alleviated when attempting to apply the analogy to military operations within cyberspace itself.
As part of our continued research within this technology space, we plan on developing some of these described use cases for further study. Attempting to apply the concept of “Key Cyber Terrain” to a well-defined and tangible set of missions should provide a valuable data corpus to help resolve some of the ambiguities that are currently stifling our efforts. Perhaps then, “Key Cyber Terrain” may cease to elude us.
Endnotes
- Sun Tzu, when discussing the importance of terrain in warfare stated: “We may distinguish six kinds of terrain, to wit: (1) Accessible ground; (2) entangling ground; (3) temporizing ground; (4) narrow passes; (5) precipitous heights; (6) positions at a great distance from the enemy.”
- As an example, in Battle of Jieting of the Three Kingdoms period of China, Shu Han forces occupied a hilltop, which opposing forces soon surrounded, isolating them from supplies and reinforcements. As a result, the Shu forces were defeated [https://en.wikipedia.org/wiki/Battle_of_Jieting].
- https://en.oxforddictionaries.com/definition/terrain
- You may have noticed, that this explanation of what is meant by “Key Cyber Terrain” does not equate to the definition of “Key Terrain” that was previously referenced. Terrain that provides a “marked advantage” is not the same as a “critical enabler” for mission execution.
- AFATDS: Advanced Field Artillery Tactical Data System
- BMDS: Ballistic Missile Defense System
- Policy discussion are beyond the scope of this document. It can be speculated that in the future existing Cyberspace Operations restrictions will be relaxed, however, there will still be significant implications (e.g. potential collateral damage, laws, force structure and capability requirements, etc.) that will still have to be considered when operating within this domain.
- The many technical challenges associated with the logical mapping of cyberspace is the subject of numerous scholarly articles.
- For example, the ability to map networking infrastructure and services to specific mission objectives has proven to be very technically challenging [5].
- Avionics data interchange standards for modern aircraft include: ARINC 429, ARINC 629, MILSTD 1553, MIL-STD 1773, CSDB and ASCB.
- The presence of a communication path that may allow such an attack is a point of some contention. According to [12], some newer aircraft may allow for some two-way communications between such systems.
- http://money.cnn.com/2013/12/22/news/companies/target-credit-card-hack/
- This question is somewhat rhetorical. The answer is of course yes, and multiple top target executives were fired because of this incident, but not because they did not properly identify their “Key Cyber Terrain”. More on this in section III.
- You may have noticed, that for this example, we have once again devolved to equating “Key Terrain” to mission critical resources. This same inclination often occurs when planning cyberspace operations; especially those that are defensive in nature.
- [7] Argues that a unit should only focus on what is within their span of control and rely on higher echelons for the rest. This is a fair point, but it does still have some significant implications. For instance, mission planning (even for relatively simple missions) would necessitate extensive cross echelon coordination and resourcing.
- The answer to this question is clearly “no”, but this does then imply that the usage of “Key Terrain” within cyberspace is not equivalent to its usage within the physical domains.
- This can work well from a Defensive Cyberspace Operations perspective where we have the ability to define the architecture of our networks; a luxury we most often do not have within gray and red operational spaces.
- OCOKA: Observation and fields of fire, Cover and concealment, Obstacles, Key or decisive terrain, Avenues of approach. http://www.armystudyguide.com/content/army_board_study_guide_topics/survival/ocoka.shtml
- The six phases of military operations are defined in Joint Publication 3-0.
References
- Department of Defense, “DOD Dictionary of Military and Associated Terms,” Defense Technical Information Center, 2017.
- J. Major Harry D. Scott, “Identification of Decisive Terrain,” School of Advanced Military Studies, Fort Leavenworth, Kansas, 1993.
- J. R. Mills, “The Key Terrain of Cyber,” Georgetown Journal of International Affairs, pp. 99-107, 2012.
- D. Raymond, G. Conti, T. Cross and M. Nowatkowski, “Key Terrain in Cybersapce: Seeking the High Ground,” in 6th International Confernece of Cyber Conflict, 2014.
- S. A. E., K. M. C. and Z. J. R., “Cyber Network Mission Dependencies,” MIT Lincoln Laboratory, Lexington, MA, 2015.
- G. L. D. W. U. (Ret.), “CYBERSPACE – The Fifth Operational Domain,” IDA Research Notes, 2011.
- S. D. Applegate, C. L. Carpenter and D. C. West, “Searching for Digital Hilltops: A Doctrinal Approach to Identifying Key Terrain in cyberspace,” Joint Force Quarterly (JFQ), vol. 84, no. 1st Quarter, pp. 18-23, 2017.
- I. BG George J. Franz, Effective Synchronization and Integration of Effects Through cyberspace for the Joint Warfighter, US CYBER COMMAND, 2014.
- M. B. T. Williams, “The Joint Force Commander’s Guide to Cyberspace Operations,” Joint Force Quarterly (JFQ), vol. 73, no. 2nd Qrt, pp. 12-19, 2nd Qrt 2014.
- T. Radichel, “CASE STUDY: Critical controls that could have prevented Target breach,” SANS institute, 2014.
- E. Perez, “FBI: Hacker claimed to have taken over flight’s engine controls,” CNN, 15 05 2015. [Online]. Available: http://www.cnn.com/2015/05/17/us/fbi-hacker-flight-computer-systems/. [Accessed 05 04 2017].
- K. Zetter, “Is it possible to hack commerical aircraft?,” WIRED, 26 05 2015. [Online]. Available: https://www.wired.com/2015/05/possible-passengers-hack-commercial-aircraft/]. . [Accessed 05 04 2017].
- M. Kassner, “Anatomy of the Target data breach: Missed opportunities and lessons learned,” ZDNet, 02 02 2015. [Online]. Available: http://www.zdnet.com/article/anatomy-of-the-target-data-breach-missed-opportunities-and-lessons-learned/. [Accessed 05 04 2017].
- D. Hobbs, “Application of OCOKA to Cyberterrain,” White Wolf Security, Lancaster, PA, 2007.


